-
Compteur de contenus
136 -
Inscription
-
Dernière visite
Messages postés par Boeldieu
-
-
Voui, mais même la Grèce est un cas extrême. Même si on est mal placés pour donner des leçons, la France est quand même loin, très loin d'être dans un état aussi grave. L'euro va tanguer, mais pas chuter. Quant à notre pays en lui-même, il garde des réserves financières très importantes (infrastructures, possessions étatiques, épargne importante…) qui le stabilisent fortement.
Le précédent historique est la chute de l'empire soviétique. Deux mois avant que ça prenne l'eau pour de bon ça semblait parti pour durer. Je fais parti d'une génération qui rigolait quand on lui demandait s'il pensait qu'un jour l'Allemagne serait réunifiée (je me souviens d'un prof de Français qui nous avait posé la question : on s'était trop moqué de lui, vraiment comme s'il nous demandais de montrer que 2+2=5). Bref l'agonie est longue, très longue, plus longue que ce à quoi on peut songer (70 ans dans le cas soviétique) mais la précipitation (quasiment dans le sens chimique du terme) est beaucoup plus rapide que celle qu'on imagine.
Dans le cas soviétique ce fut bien un armaggedon (ou un teotwawki politique) qui a eu lieu. Je pense que notre système Keynésien va subir le même sort avec la différence qu'on n'a pas vraiment de "modèle" concurrent sur lequel se raccrocher. On entre dans une période chaotique et personne ne peut dire ce qui va en sortir.
-
Au début de la crise, on avait droit tous les 3 mois à un "sommet européen de la dernière chance" que s'il ratait, promis juré craché c'était l'apocalypse pour tout le monde.
Maintenant, on a droit tous les 3 mois à des études qui nous disent qu'il nous reste 3 mois à vivre.
Sans vouloir être optimiste face à ce système pourri et aux branquignoles qui nous gouvernent, j'ai du mal à trouver encore une crédibilité dans ce genre d'annonce. Si ça se trouve c'est vrai, cette fois c'est la bonne, dans 3 mois on va tous crever. Sauf qu'à l'avoir annoncé 3894 fois, je n'arrive pas à croire que la 3895e soit la bonne.
Pour l'instant, je reste plutôt convaincu qu'on se dirige vers une conjoncture merdique, avec dégradation lente, déclin européen et pourrissement généralisé encouragé par nos fonctio-politiciens d'élite, mais sans armageddon économique pour tout défoncer aussi à une vitesse aussi réaliste que celle d'un film de Roland Emmerich.
Bien sûr ça ne va pas exploser en vol. Ma mère en revenant d'une semaine passée en Grèce me décrivait plutôt une impression de dépression généralisée (escalator et tourniquets arrêtés dans les aéroports, petits vieux qui vivent sous perfusion de la famille vu la fonte des retraites etc.) : c'est déjà la grosse merde là bas. Et c'est parti pour durer. Ce qui nous pend au nez est un déclassement. Très probablement c'est quasiment une génération (au mieux) qui va bouffer de la merde pour rattraper le coup. Et si l'Armaggedon ne durait qu'une fraction de seconde finalement ce ne serait pas si terrible…
Ce qui est clair est que lundi prochain on verra si on a droit à un Grexit ou pas suivant si il y a un front républicain contre le FN Syriza prend le pouvoir. Ca fait une date précise à prendre en compte. Les législatives françaises sont un épiphénomène sans un intérêt.
-
Le début de la faim ? En tout cas ils n'ont même plus de raisins à Corinthe : http://chasvoice.blogspot.fr/2012/06/destitution-and-hunger-in-greek-prisons.html?m=1
Destitution and Hunger In Greek Prisons: “Not Even One Grain of Rice Left In Warehouses”
The Daily Sheeple
All
indications suggest that basic services in Greece have begun to break down, with reports from several Greek prisons and military installations indicating that prisoners are malnourished and starving. Food shortages caused by austerity related spending cuts and truck stoppages are also reportedly reducing daily rations for soldiers stationed in the area of Corinth, Greece.
-
D'ailleurs des backdoors dans les circuits imprimés ça existe… : https://www.cl.cam.ac.uk/~sps32/sec_news.html#Assurance
Current issues. UK officials are fearful that China has the capability to shut down businesses, military and critical infrastructure through cyber attacks and spy equipment embedded in computer and telecommunications equipment. The Stuxnet worm is the most famous and best case example of a cyber attack on a network which wreaked devastation having easily compromised conventional software defensive systems. There have been many cases of computer hardware having backdoors, Trojans or other programs to allow an attacker to gain access or transmit confidential data to a third party. Considerable focus and expense has been invested in software computer networks and system defences to detect and eradicate such threats.
However, similar technology with antivirus or anti Trojan capability for hardware (silicon chips) is not available. The computer or network hardware underpins and runs all the software defence systems. If the hardware has a vulnerability then all the energy in defending at the software level is redundant. An effort must be made to defend and detect at the hardware level for a more comprehensive strategy.
Our findings. Claims were made by the intelligence agencies around the world, from MI5, NSA and IARPA, that silicon chips could be infected. We developed breakthrough silicon chip scanning technology to investigate these claims. We chose an American military chip that is highly secure with sophisticated encryption standard, manufactured in China. Our aim was to perform advanced code breaking and to see if there were any unexpected features on the chip. We scanned the silicon chip in an affordable time and found a previously unknown backdoor inserted by the manufacturer. This backdoor has a key, which we were able to extract. If you use this key you can disable the chip or reprogram it at will, even if locked by the user with their own key. This particular chip is prevalent in many systems from weapons, nuclear power plants to public transport. In other words, this backdoor access could be turned into an advanced Stuxnet weapon to attack potentially millions of systems. The scale and range of possible attacks has huge implications for National Security and public infrastructure.
Key features of our technology:
scans silicon/hardware for backdoors, Trojans and unexpected behaviour
low cost
very fast result turnaround time
high portability
adaptable - scale up to include many types of chip
Further funding is needed for us to progress to testing further silicon chips and to develop better search algorithms which would allow us to detect possible spy systems or vulnerabilities in a greater range of systems.
Currently there is no economical or timely way of ascertaining if a manufacturer's specifications have been altered during the manufacturing process (99% of chips are manufactured in China), or indeed if the specifications themselves contain a deliberately inserted potential threat.
Conclusions. It is clear that cyber attacks will increasingly be of this nature, having most impact; it is imperative that this issue is addressed as a matter of urgency. We would suggest making hardware assurance (HWA) & hardware defence (HWD), the testing of silicon chips for backdoors and Trojans, and their defence, a greater priority within the National Cyber Strategy. Until now it was not possible to perform such analysis in a timely or cost effective manner. Our technology provides a solution. A variation in this technology could be used as a backstop defence on a computer or network system where it can monitor instructions and possible reprogramming or activation of a buried spy system in a real time environment, thereby preventing Stuxnet type attacks.
Further funding is needed for us to progress to testing further silicon chips and to develop better search algorithms which would allow us to detect possible spy systems or vulnerabilities in a greater range of systems.
-
L'automatisation de la chaîne de coercition se poursuit : http://www.nytimes.com/2012/05/29/world/obamas-leadership-in-war-on-al-qaeda.html?hp&pagewanted=all
On commence par faire une liste (Kill by click ?), de là à la filer directement sur des drones qui tournent en rond ça ne va pas prendre des siècles à se réaliser.
This was the enemy, served up in the latest chart from the intelligence agencies: 15 Qaeda suspects in Yemen with Western ties. The mug shots and brief biographies resembled a high school yearbook layout. Several were Americans. Two were teenagers, including a girl who looked even younger than her 17 years.
President Obama, overseeing the regular Tuesday counterterrorism meeting of two dozen security officials in the White House Situation Room, took a moment to study the faces. It was Jan. 19, 2010, the end of a first year in office punctuated by terrorist plots and culminating in a brush with catastrophe over Detroit on Christmas Day, a reminder that a successful attack could derail his presidency. Yet he faced adversaries without uniforms, often indistinguishable from the civilians around them.
“How old are these people?” he asked, according to two officials present. “If they are starting to use children,” he said of Al Qaeda, “we are moving into a whole different phase.”
It was not a theoretical question: Mr. Obama has placed himself at the helm of a top secret “nominations” process to designate terrorists for kill or capture, of which the capture part has become largely theoretical. He had vowed to align the fight against Al Qaeda with American values; the chart, introducing people whose deaths he might soon be asked to order, underscored just what a moral and legal conundrum this could be.
Mr. Obama is the liberal law professor who campaigned against the Iraq war and torture, and then insisted on approving every new name on an expanding “kill list,” poring over terrorist suspects’ biographies on what one official calls the macabre “baseball cards” of an unconventional war. When a rare opportunity for a drone strike at a top terrorist arises — but his family is with him — it is the president who has reserved to himself the final moral calculation.
“He is determined that he will make these decisions about how far and wide these operations will go,” said Thomas E. Donilon, his national security adviser. “His view is that he’s responsible for the position of the United States in the world.” He added, “He’s determined to keep the tether pretty short.”
Nothing else in Mr. Obama’s first term has baffled liberal supporters and confounded conservative critics alike as his aggressive counterterrorism record. His actions have often remained inscrutable, obscured by awkward secrecy rules, polarized political commentary and the president’s own deep reserve.
In interviews with The New York Times, three dozen of his current and former advisers described Mr. Obama’s evolution since taking on the role, without precedent in presidential history, of personally overseeing the shadow war with Al Qaeda.
They describe a paradoxical leader who shunned the legislative deal-making required to close the detention facility at Guantánamo Bay in Cuba, but approves lethal action without hand-wringing. While he was adamant about narrowing the fight and improving relations with the Muslim world, he has followed the metastasizing enemy into new and dangerous lands. When he applies his lawyering skills to counterterrorism, it is usually to enable, not constrain, his ferocious campaign against Al Qaeda — even when it comes to killing an American cleric in Yemen, a decision that Mr. Obama told colleagues was “an easy one.”
His first term has seen private warnings from top officials about a “Whac-A-Mole” approach to counterterrorism; the invention of a new category of aerial attack following complaints of careless targeting; and presidential acquiescence in a formula for counting civilian deaths that some officials think is skewed to produce low numbers.
The administration’s failure to forge a clear detention policy has created the impression among some members of Congress of a take-no-prisoners policy. And Mr. Obama’s ambassador to Pakistan, Cameron P. Munter, has complained to colleagues that the C.I.A.’s strikes drive American policy there, saying “he didn’t realize his main job was to kill people,” a colleague said.
Beside the president at every step is his counterterrorism adviser, John O. Brennan, who is variously compared by colleagues to a dogged police detective, tracking terrorists from his cavelike office in the White House basement, or a priest whose blessing has become indispensable to Mr. Obama, echoing the president’s attempt to apply the “just war” theories of Christian philosophers to a brutal modern conflict.
But the strikes that have eviscerated Al Qaeda — just since April, there have been 14 in Yemen, and 6 in Pakistan — have also tested both men’s commitment to the principles they have repeatedly said are necessary to defeat the enemy in the long term. Drones have replaced Guantánamo as the recruiting tool of choice for militants; in his 2010 guilty plea, Faisal Shahzad, who had tried to set off a car bomb in Times Square, justified targeting civilians by telling the judge, “When the drones hit, they don’t see children.”
Dennis C. Blair, director of national intelligence until he was fired in May 2010, said that discussions inside the White House of long-term strategy against Al Qaeda were sidelined by the intense focus on strikes. “The steady refrain in the White House was, ‘This is the only game in town’ — reminded me of body counts in Vietnam,” said Mr. Blair, a retired admiral who began his Navy service during that war.
Mr. Blair’s criticism, dismissed by White House officials as personal pique, nonetheless resonates inside the government.
William M. Daley, Mr. Obama’s chief of staff in 2011, said the president and his advisers understood that they could not keep adding new names to a kill list, from ever lower on the Qaeda totem pole. What remains unanswered is how much killing will be enough.
“One guy gets knocked off, and the guy’s driver, who’s No. 21, becomes 20?” Mr. Daley said, describing the internal discussion. “At what point are you just filling the bucket with numbers?”
‘Maintain My Options’
A phalanx of retired generals and admirals stood behind Mr. Obama on the second day of his presidency, providing martial cover as he signed several executive orders to make good on campaign pledges. Brutal interrogation techniques were banned, he declared. And the prison at Guantánamo Bay would be closed.
What the new president did not say was that the orders contained a few subtle loopholes. They reflected a still unfamiliar Barack Obama, a realist who, unlike some of his fervent supporters, was never carried away by his own rhetoric. Instead, he was already putting his lawyerly mind to carving out the maximum amount of maneuvering room to fight terrorism as he saw fit.
It was a pattern that would be seen repeatedly, from his response to Republican complaints that he wanted to read terrorists their rights, to his acceptance of the C.I.A.’s method for counting civilian casualties in drone strikes.
The day before the executive orders were issued, the C.I.A.’s top lawyer, John A. Rizzo, had called the White House in a panic. The order prohibited the agency from operating detention facilities, closing once and for all the secret overseas “black sites” where interrogators had brutalized terrorist suspects.
“The way this is written, you are going to take us out of the rendition business,” Mr. Rizzo told Gregory B. Craig, Mr. Obama’s White House counsel, referring to the much-criticized practice of grabbing a terrorist suspect abroad and delivering him to another country for interrogation or trial. The problem, Mr. Rizzo explained, was that the C.I.A. sometimes held such suspects for a day or two while awaiting a flight. The order appeared to outlaw that.
Mr. Craig assured him that the new president had no intention of ending rendition — only its abuse, which could lead to American complicity in torture abroad. So a new definition of “detention facility” was inserted, excluding places used to hold people “on a short-term, transitory basis.” Problem solved — and no messy public explanation damped Mr. Obama’s celebration.
“Pragmatism over ideology,” his campaign national security team had advised in a memo in March 2008. It was counsel that only reinforced the president’s instincts.
Even before he was sworn in, Mr. Obama’s advisers had warned him against taking a categorical position on what would be done with Guantánamo detainees. The deft insertion of some wiggle words in the president’s order showed that the advice was followed.
Some detainees would be transferred to prisons in other countries, or released, it said. Some would be prosecuted — if “feasible” — in criminal courts. Military commissions, which Mr. Obama had criticized, were not mentioned — and thus not ruled out.
As for those who could not be transferred or tried but were judged too dangerous for release? Their “disposition” would be handled by “lawful means, consistent with the national security and foreign policy interests of the United States and the interests of justice.”
A few sharp-eyed observers inside and outside the government understood what the public did not. Without showing his hand, Mr. Obama had preserved three major policies — rendition, military commissions and indefinite detention — that have been targets of human rights groups since the 2001 terrorist attacks.
But a year later, with Congress trying to force him to try all terrorism suspects using revamped military commissions, he deployed his legal skills differently — to preserve trials in civilian courts.
It was shortly after Dec. 25, 2009, following a close call in which a Qaeda-trained operative named Umar Farouk Abdulmutallab had boarded a Detroit-bound airliner with a bomb sewn into his underwear.
Mr. Obama was taking a drubbing from Republicans over the government’s decision to read the suspect his rights, a prerequisite for bringing criminal charges against him in civilian court.
The president “seems to think that if he gives terrorists the rights of Americans, lets them lawyer up and reads them their Miranda rights, we won’t be at war,” former Vice President Dick Cheney charged.
Sensing vulnerability on both a practical and political level, the president summoned his attorney general, Eric H. Holder Jr., to the White House.
F.B.I. agents had questioned Mr. Abdulmutallab for 50 minutes and gained valuable intelligence before giving him the warning. They had relied on a 1984 case called New York v. Quarles, in which the Supreme Court ruled that statements made by a suspect in response to urgent public safety questions — the case involved the location of a gun — could be introduced into evidence even if the suspect had not been advised of the right to remain silent.
Mr. Obama, who Mr. Holder said misses the legal profession, got into a colloquy with the attorney general. How far, he asked, could Quarles be stretched? Mr. Holder felt that in terrorism cases, the court would allow indefinite questioning on a fairly broad range of subjects.
Satisfied with the edgy new interpretation, Mr. Obama gave his blessing, Mr. Holder recalled.
“Barack Obama believes in options: ‘Maintain my options,’ “ said Jeh C. Johnson, a campaign adviser and now general counsel of the Defense Department.
‘They Must All Be Militants’
That same mind-set would be brought to bear as the president intensified what would become a withering campaign to use unmanned aircraft to kill Qaeda terrorists.
Just days after taking office, the president got word that the first strike under his administration had killed a number of innocent Pakistanis. “The president was very sharp on the thing, and said, ‘I want to know how this happened,’ “ a top White House adviser recounted.
In response to his concern, the C.I.A. downsized its munitions for more pinpoint strikes. In addition, the president tightened standards, aides say: If the agency did not have a “near certainty” that a strike would result in zero civilian deaths, Mr. Obama wanted to decide personally whether to go ahead.
The president’s directive reinforced the need for caution, counterterrorism officials said, but did not significantly change the program. In part, that is because “the protection of innocent life was always a critical consideration,” said Michael V. Hayden, the last C.I.A. director under President George W. Bush.
It is also because Mr. Obama embraced a disputed method for counting civilian casualties that did little to box him in. It in effect counts all military-age males in a strike zone as combatants, according to several administration officials, unless there is explicit intelligence posthumously proving them innocent.
Counterterrorism officials insist this approach is one of simple logic: people in an area of known terrorist activity, or found with a top Qaeda operative, are probably up to no good. “Al Qaeda is an insular, paranoid organization — innocent neighbors don’t hitchhike rides in the back of trucks headed for the border with guns and bombs,” said one official, who requested anonymity to speak about what is still a classified program.
This counting method may partly explain the official claims of extraordinarily low collateral deaths. In a speech last year Mr. Brennan, Mr. Obama’s trusted adviser, said that not a single noncombatant had been killed in a year of strikes. And in a recent interview, a senior administration official said that the number of civilians killed in drone strikes in Pakistan under Mr. Obama was in the “single digits” — and that independent counts of scores or hundreds of civilian deaths unwittingly draw on false propaganda claims by militants.
But in interviews, three former senior intelligence officials expressed disbelief that the number could be so low. The C.I.A. accounting has so troubled some administration officials outside the agency that they have brought their concerns to the White House. One called it “guilt by association” that has led to “deceptive” estimates of civilian casualties.
“It bothers me when they say there were seven guys, so they must all be militants,” the official said. “They count the corpses and they’re not really sure who they are.”
‘A No-Brainer’
About four months into his presidency, as Republicans accused him of reckless naïveté on terrorism, Mr. Obama quickly pulled together a speech defending his policies. Standing before the Constitution at the National Archives in Washington, he mentioned Guantánamo 28 times, repeating his campaign pledge to close the prison.
But it was too late, and his defensive tone suggested that Mr. Obama knew it. Though President George W. Bush and Senator John McCain, the 2008 Republican candidate, had supported closing the Guantánamo prison, Republicans in Congress had reversed course and discovered they could use the issue to portray Mr. Obama as soft on terrorism.
Walking out of the Archives, the president turned to his national security adviser at the time, Gen. James L. Jones, and admitted that he had never devised a plan to persuade Congress to shut down the prison.
“We’re never going to make that mistake again,” Mr. Obama told the retired Marine general.
General Jones said the president and his aides had assumed that closing the prison was “a no-brainer — the United States will look good around the world.” The trouble was, he added, “nobody asked, ‘O.K., let’s assume it’s a good idea, how are you going to do this?’ “
It was not only Mr. Obama’s distaste for legislative backslapping and arm-twisting, but also part of a deeper pattern, said an administration official who has watched him closely: the president seemed to have “a sense that if he sketches a vision, it will happen — without his really having thought through the mechanism by which it will happen.”
In fact, both Secretary of State Hillary Rodham Clinton and the attorney general, Mr. Holder, had warned that the plan to close the Guantánamo prison was in peril, and they volunteered to fight for it on Capitol Hill, according to officials. But with Mr. Obama’s backing, his chief of staff, Rahm Emanuel, blocked them, saying health care reform had to go first.
When the administration floated a plan to transfer from Guantánamo to Northern Virginia two Uighurs, members of a largely Muslim ethnic minority from China who are considered no threat to the United States, Virginia Republicans led by Representative Frank R. Wolf denounced the idea. The administration backed down.
That show of weakness doomed the effort to close Guantánamo, the same administration official said. “Lyndon Johnson would have steamrolled the guy,” he said. “That’s not what happened. It’s like a boxing match where a cut opens over a guy’s eye.”
The Use of Force
It is the strangest of bureaucratic rituals: Every week or so, more than 100 members of the government’s sprawling national security apparatus gather, by secure video teleconference, to pore over terrorist suspects’ biographies and recommend to the president who should be the next to die.
This secret “nominations” process is an invention of the Obama administration, a grim debating society that vets the PowerPoint slides bearing the names, aliases and life stories of suspected members of Al Qaeda’s branch in Yemen or its allies in Somalia’s Shabab militia.
The video conferences are run by the Pentagon, which oversees strikes in those countries, and participants do not hesitate to call out a challenge, pressing for the evidence behind accusations of ties to Al Qaeda.
“What’s a Qaeda facilitator?” asked one participant, illustrating the spirit of the exchanges. “If I open a gate and you drive through it, am I a facilitator?” Given the contentious discussions, it can take five or six sessions for a name to be approved, and names go off the list if a suspect no longer appears to pose an imminent threat, the official said. A parallel, more cloistered selection process at the C.I.A. focuses largely on Pakistan, where that agency conducts strikes.
The nominations go to the White House, where by his own insistence and guided by Mr. Brennan, Mr. Obama must approve any name. He signs off on every strike in Yemen and Somalia and also on the more complex and risky strikes in Pakistan — about a third of the total.
Aides say Mr. Obama has several reasons for becoming so immersed in lethal counterterrorism operations. A student of writings on war by Augustine and Thomas Aquinas, he believes that he should take moral responsibility for such actions. And he knows that bad strikes can tarnish America’s image and derail diplomacy.
“He realizes this isn’t science, this is judgments made off of, most of the time, human intelligence,” said Mr. Daley, the former chief of staff. “The president accepts as a fact that a certain amount of screw-ups are going to happen, and to him, that calls for a more judicious process.”
But the control he exercises also appears to reflect Mr. Obama’s striking self-confidence: he believes, according to several people who have worked closely with him, that his own judgment should be brought to bear on strikes.
Asked what surprised him most about Mr. Obama, Mr. Donilon, the national security adviser, answered immediately: “He’s a president who is quite comfortable with the use of force on behalf of the United States.”
In fact, in a 2007 campaign speech in which he vowed to pull the United States out of Iraq and refocus on Al Qaeda, Mr. Obama had trumpeted his plan to go after terrorist bases in Pakistan — even if Pakistani leaders objected. His rivals at the time, including Mitt Romney, Joseph R. Biden Jr. and Mrs. Clinton, had all pounced on what they considered a greenhorn’s campaign bluster. (Mr. Romney said Mr. Obama had become “Dr. Strangelove.”)
In office, however, Mr. Obama has done exactly what he had promised, coming quickly to rely on the judgment of Mr. Brennan.
Mr. Brennan, a son of Irish immigrants, is a grizzled 25-year veteran of the C.I.A. whose work as a top agency official during the brutal interrogations of the Bush administration made him a target of fierce criticism from the left. He had been forced, under fire, to withdraw his name from consideration to lead the C.I.A. under Mr. Obama, becoming counterterrorism chief instead.
Some critics of the drone strategy still vilify Mr. Brennan, suggesting that he is the C.I.A.’s agent in the White House, steering Mr. Obama to a targeted killing strategy. But in office, Mr. Brennan has surprised many former detractors by speaking forcefully for closing Guantánamo and respecting civil liberties.
Harold H. Koh, for instance, as dean of Yale Law School was a leading liberal critic of the Bush administration’s counterterrorism policies. But since becoming the State Department’s top lawyer, Mr. Koh said, he has found in Mr. Brennan a principled ally.
“If John Brennan is the last guy in the room with the president, I’m comfortable, because Brennan is a person of genuine moral rectitude,” Mr. Koh said. “It’s as though you had a priest with extremely strong moral values who was suddenly charged with leading a war.”
The president values Mr. Brennan’s experience in assessing intelligence, from his own agency or others, and for the sobriety with which he approaches lethal operations, other aides say.
“The purpose of these actions is to mitigate threats to U.S. persons’ lives,” Mr. Brennan said in an interview. “It is the option of last recourse. So the president, and I think all of us here, don’t like the fact that people have to die. And so he wants to make sure that we go through a rigorous checklist: The infeasibility of capture, the certainty of the intelligence base, the imminence of the threat, all of these things.”
Yet the administration’s very success at killing terrorism suspects has been shadowed by a suspicion: that Mr. Obama has avoided the complications of detention by deciding, in effect, to take no prisoners alive. While scores of suspects have been killed under Mr. Obama, only one has been taken into American custody, and the president has balked at adding new prisoners to Guantánamo.
“Their policy is to take out high-value targets, versus capturing high-value targets,” said Senator Saxby Chambliss of Georgia, the top Republican on the intelligence committee. “They are not going to advertise that, but that’s what they are doing.”
Mr. Obama’s aides deny such a policy, arguing that capture is often impossible in the rugged tribal areas of Pakistan and Yemen and that many terrorist suspects are in foreign prisons because of American tips. Still, senior officials at the Justice Department and the Pentagon acknowledge that they worry about the public perception.
“We have to be vigilant to avoid a no-quarter, or take-no-prisoners policy,” said Mr. Johnson, the Pentagon’s chief lawyer.
Trade-Offs
The care that Mr. Obama and his counterterrorism chief take in choosing targets, and their reliance on a precision weapon, the drone, reflect his pledge at the outset of his presidency to reject what he called the Bush administration’s “false choice between our safety and our ideals.”
But he has found that war is a messy business, and his actions show that pursuing an enemy unbound by rules has required moral, legal and practical trade-offs that his speeches did not envision.
One early test involved Baitullah Mehsud, the leader of the Pakistani Taliban. The case was problematic on two fronts, according to interviews with both administration and Pakistani sources.
The C.I.A. worried that Mr. Mehsud, whose group then mainly targeted the Pakistan government, did not meet the Obama administration’s criteria for targeted killing: he was not an imminent threat to the United States. But Pakistani officials wanted him dead, and the American drone program rested on their tacit approval. The issue was resolved after the president and his advisers found that he represented a threat, if not to the homeland, to American personnel in Pakistan.
Then, in August 2009, the C.I.A. director, Leon E. Panetta, told Mr. Brennan that the agency had Mr. Mehsud in its sights. But taking out the Pakistani Taliban leader, Mr. Panetta warned, did not meet Mr. Obama’s standard of “near certainty” of no innocents being killed. In fact, a strike would certainly result in such deaths: he was with his wife at his in-laws’ home.
“Many times,” General Jones said, in similar circumstances, “at the 11th hour we waved off a mission simply because the target had people around them and we were able to loiter on station until they didn’t.”
But not this time. Mr. Obama, through Mr. Brennan, told the C.I.A. to take the shot, and Mr. Mehsud was killed, along with his wife and, by some reports, other family members as well, said a senior intelligence official.
The attempted bombing of an airliner a few months later, on Dec. 25, stiffened the president’s resolve, aides say. It was the culmination of a series of plots, including the killing of 13 people at Fort Hood, Tex. by an Army psychiatrist who had embraced radical Islam.
Mr. Obama is a good poker player, but he has a tell when he is angry. His questions become rapid-fire, said his attorney general, Mr. Holder. “He’ll inject the phrase, ‘I just want to make sure you understand that.’ “ And it was clear to everyone, Mr. Holder said, that he was simmering about how a 23-year-old bomber had penetrated billions of dollars worth of American security measures.
When a few officials tentatively offered a defense, noting that the attack had failed because the terrorists were forced to rely on a novice bomber and an untested formula because of stepped-up airport security, Mr. Obama cut them short.
“Well, he could have gotten it right and we’d all be sitting here with an airplane that blew up and killed over a hundred people,” he said, according to a participant. He asked them to use the close call to imagine in detail the consequences if the bomb had detonated. In characteristic fashion, he went around the room, asking each official to explain what had gone wrong and what needed to be done about it.
“After that, as president, it seemed like he felt in his gut the threat to the United States,” said Michael E. Leiter, then director of the National Counterterrorism Center. “Even John Brennan, someone who was already a hardened veteran of counterterrorism, tightened the straps on his rucksack after that.”
David Axelrod, the president’s closest political adviser, began showing up at the “Terror Tuesday” meetings, his unspeaking presence a visible reminder of what everyone understood: a successful attack would overwhelm the president’s other aspirations and achievements.
In the most dramatic possible way, the Fort Hood shootings in November and the attempted Christmas Day bombing had shown the new danger from Yemen. Mr. Obama, who had rejected the Bush-era concept of a global war on terrorism and had promised to narrow the American focus to Al Qaeda’s core, suddenly found himself directing strikes in another complicated Muslim country.
The very first strike under his watch in Yemen, on Dec. 17, 2009, offered a stark example of the difficulties of operating in what General Jones described as an “embryonic theater that we weren’t really familiar with.”
It killed not only its intended target, but also two neighboring families, and left behind a trail of cluster bombs that subsequently killed more innocents. It was hardly the kind of precise operation that Mr. Obama favored. Videos of children’s bodies and angry tribesmen holding up American missile parts flooded You Tube, fueling a ferocious backlash that Yemeni officials said bolstered Al Qaeda.
The sloppy strike shook Mr. Obama and Mr. Brennan, officials said, and once again they tried to impose some discipline.
In Pakistan, Mr. Obama had approved not only “personality” strikes aimed at named, high-value terrorists, but “signature” strikes that targeted training camps and suspicious compounds in areas controlled by militants.
But some State Department officials have complained to the White House that the criteria used by the C.I.A. for identifying a terrorist “signature” were too lax. The joke was that when the C.I.A. sees “three guys doing jumping jacks,” the agency thinks it is a terrorist training camp, said one senior official. Men loading a truck with fertilizer could be bombmakers — but they might also be farmers, skeptics argued.
Now, in the wake of the bad first strike in Yemen, Mr. Obama overruled military and intelligence commanders who were pushing to use signature strikes there as well.
“We are not going to war with Yemen,” he admonished in one meeting, according to participants.
His guidance was formalized in a memo by General Jones, who called it a “governor, if you will, on the throttle,” intended to remind everyone that “one should not assume that it’s just O.K. to do these things because we spot a bad guy somewhere in the world.”
Mr. Obama had drawn a line. But within two years, he stepped across it. Signature strikes in Pakistan were killing a large number of terrorist suspects, even when C.I.A. analysts were not certain beforehand of their presence. And in Yemen, roiled by the Arab Spring unrest, the Qaeda affiliate was seizing territory.
Today, the Defense Department can target suspects in Yemen whose names they do not know. Officials say the criteria are tighter than those for signature strikes, requiring evidence of a threat to the United States, and they have even given them a new name — TADS, for Terrorist Attack Disruption Strikes. But the details are a closely guarded secret — part of a pattern for a president who came into office promising transparency.
The Ultimate Test
On that front, perhaps no case would test Mr. Obama’s principles as starkly as that of Anwar al-Awlaki, an American-born cleric and Qaeda propagandist hiding in Yemen, who had recently risen to prominence and had taunted the president by name in some of his online screeds.
The president “was very interested in obviously trying to understand how a guy like Awlaki developed,” said General Jones. The cleric’s fiery sermons had helped inspire a dozen plots, including the shootings at Fort Hood. Then he had gone “operational,” plotting with Mr. Abdulmutallab and coaching him to ignite his explosives only after the airliner was over the United States.
That record, and Mr. Awlaki’s calls for more attacks, presented Mr. Obama with an urgent question: Could he order the targeted killing of an American citizen, in a country with which the United States was not at war, in secret and without the benefit of a trial?
The Justice Department’s Office of Legal Counsel prepared a lengthy memo justifying that extraordinary step, asserting that while the Fifth Amendment’s guarantee of due process applied, it could be satisfied by internal deliberations in the executive branch.
Mr. Obama gave his approval, and Mr. Awlaki was killed in September 2011, along with a fellow propagandist, Samir Khan, an American citizen who was not on the target list but was traveling with him.
If the president had qualms about this momentous step, aides said he did not share them. Mr. Obama focused instead on the weight of the evidence showing that the cleric had joined the enemy and was plotting more terrorist attacks.
“This is an easy one,” Mr. Daley recalled him saying, though the president warned that in future cases, the evidence might well not be so clear.
In the wake of Mr. Awlaki’s death, some administration officials, including the attorney general, argued that the Justice Department’s legal memo should be made public. In 2009, after all, Mr. Obama had released Bush administration legal opinions on interrogation over the vociferous objections of six former C.I.A. directors.
This time, contemplating his own secrets, he chose to keep the Awlaki opinion secret.
“Once it’s your pop stand, you look at things a little differently,” said Mr. Rizzo, the C.I.A.’s former general counsel.
Mr. Hayden, the former C.I.A. director and now an adviser to Mr. Obama’s Republican challenger, Mr. Romney, commended the president’s aggressive counterterrorism record, which he said had a “Nixon to China” quality. But, he said, “secrecy has its costs” and Mr. Obama should open the strike strategy up to public scrutiny.
“This program rests on the personal legitimacy of the president, and that’s not sustainable,” Mr. Hayden said. “I have lived the life of someone taking action on the basis of secret O.L.C. memos, and it ain’t a good life. Democracies do not make war on the basis of legal memos locked in a D.O.J. safe.”
Tactics Over Strategy
In his June 2009 speech in Cairo, aimed at resetting relations with the Muslim world, Mr. Obama had spoken eloquently of his childhood years in Indonesia, hearing the call to prayer “at the break of dawn and the fall of dusk.”
“The United States is not — and never will be — at war with Islam,” he declared.
But in the months that followed, some officials felt the urgency of counterterrorism strikes was crowding out consideration of a broader strategy against radicalization. Though Mrs. Clinton strongly supported the strikes, she complained to colleagues about the drones-only approach at Situation Room meetings, in which discussion would focus exclusively on the pros, cons and timing of particular strikes.
At their weekly lunch, Mrs. Clinton told the president she thought there should be more attention paid to the root causes of radicalization, and Mr. Obama agreed. But it was September 2011 before he issued an executive order setting up a sophisticated, interagency war room at the State Department to counter the jihadi narrative on an hour-by-hour basis, posting messages and video online and providing talking points to embassies.
Mr. Obama was heartened, aides say, by a letter discovered in the raid on Osama bin Laden’s compound in Pakistan. It complained that the American president had undermined Al Qaeda’s support by repeatedly declaring that the United States was at war not with Islam, but with the terrorist network. “We must be doing a good job,” Mr. Obama told his secretary of state.
Moreover, Mr. Obama’s record has not drawn anything like the sweeping criticism from allies that his predecessor faced. John B. Bellinger III, a top national security lawyer under the Bush administration, said that was because Mr. Obama’s liberal reputation and “softer packaging” have protected him. “After the global outrage over Guantánamo, it’s remarkable that the rest of the world has looked the other way while the Obama administration has conducted hundreds of drone strikes in several different countries, including killing at least some civilians,” said Mr. Bellinger, who supports the strikes.
By withdrawing from Iraq and preparing to withdraw from Afghanistan, Mr. Obama has refocused the fight on Al Qaeda and hugely reduced the death toll both of American soldiers and Muslim civilians. But in moments of reflection, Mr. Obama may have reason to wonder about unfinished business and unintended consequences.
His focus on strikes has made it impossible to forge, for now, the new relationship with the Muslim world that he had envisioned. Both Pakistan and Yemen are arguably less stable and more hostile to the United States than when Mr. Obama became president.
Justly or not, drones have become a provocative symbol of American power, running roughshod over national sovereignty and killing innocents. With China and Russia watching, the United States has set an international precedent for sending drones over borders to kill enemies.
Mr. Blair, the former director of national intelligence, said the strike campaign was dangerously seductive. “It is the politically advantageous thing to do — low cost, no U.S. casualties, gives the appearance of toughness,” he said. “It plays well domestically, and it is unpopular only in other countries. Any damage it does to the national interest only shows up over the long term.”
But Mr. Blair’s dissent puts him in a small minority of security experts. Mr. Obama’s record has eroded the political perception that Democrats are weak on national security. No one would have imagined four years ago that his counterterrorism policies would come under far more fierce attack from the American Civil Liberties Union than from Mr. Romney.
Aides say that Mr. Obama’s choices, though, are not surprising. The president’s reliance on strikes, said Mr. Leiter, the former head of the National Counterterrorism Center, “is far from a lurid fascination with covert action and special forces. It’s much more practical. He’s the president. He faces a post-Abdulmutallab situation, where he’s being told people might attack the United States tomorrow.”
“You can pass a lot of laws,” Mr. Leiter said, “Those laws are not going to get Bin Laden dead.”
-
Bon, sur quels sites étrangers peut-on trouver des sondages pour le second tour ? Naturellement, ce n'est pas pour les consulter, c'est illégal, hein.

Traditionnellement j'utilise la Tribune de Genève pour m'informer : www.tdg.ch
-
LOL Gödel, il est mis a toutes les sauces, de deux choses l’unes, l’humain n’est pas capable d’avoir une conscience ‘humaine’ ou il n’est pas impossible d’avoir une IA à conscience ‘humaine’, il ne faut pas confondre la possibilité hypothétique d’avoir un jour un brain in a box et la possibilité de comprendre son fonctionnement, encore moins de le poser sous forme de règles formelles.
Justement une IA peut toujours se formaliser. Mais si tu penses que l'argument n'est pas recevable… Je donne quand même les pointeurs suivants de Jean-Yves Girard (qui a démontré la cohérence de l'arithmétique du second ordre entre autre) ou de Penrose
Accessoirement, il n’est pas du tout nécessaire d’avoir un postulat matérialiste fort pour que ça soit vrai, même si la conscience n’est pas ‘dans’ la matière mais en est une propriété spirituelle émergente, ça ne signifie pas qu’elle ne peut émerger que de la viande, et si la conscience est insufflée par Dieu, qui aurai l’impudence de Lui dire qu’il n’a pas le droit de l’insuffler dans du silicium et que c’est réservé au meatbags ?
Je n'aurais pas l'impudence de lui dire quoique ce soit mais juste de faire remarquer quelques résultats de base en calculabilité montrent les limites indépassables de l'IA quoiqu'on puisse espérer en termes de développements technologiques. Et quoi que vous en pensiez ces résultats sont le résultat direct de l'incomplétude (Turing a 'inventé sa machine en travaillant sur la question de la décidabilité, question liée à celle de la complétude mais différente : pour la complétude c'est que tout ce qui est vrai est démontrable et pour la décidabilité c'est de savoir si une machine peut dire si oui ou non un théorème est vrai/démontrable).
-
Même punition pour l'intelligence artificielle: il y a 30 ans, on prédisait que l'intelligence artificielle aurait dépassé le cerveau humain avant l'an 2000.
Sauf que pour l'IA on sait depuis … les années 30 que ça marchera jamais comme on peut l'espérer (ou le craindre). Incomplétude de l’arithmétique du second ordre, Gödel toussa.
Moi je prend le paris suivant : si on arrive à simuler le fonctionnement complet d'une cellule d'ici 30 ans ce sera déjà bien…
-
Je serais le seul à utiliser emacs ?
Sinon j'utilise tout ce qui me tombe sous la main mais emacs+latex sont les premiers trucs que j'installe sur un nouvel ordi.
-
Les fabricants d'arme ?

http://www.zerohedge.com/news/fourth-largest-gun-maker-us-out-guns
-
ce serait interessant d'ailleurs de faire un post sur les moyens de fichage, et les differents fichier existant ou en projet. Et ce faisant lister aussi les moyens d'en parler…
Il y a déjà un fil "Etat et surveillance" : http://www.liberaux.org/topic/34994-etat-et-surveillance/
-
Une initiative des pirates projetant d'utiliser des drones… Comme quoi la convergence numérique peut prendre des tours inattendus:
http://thehackernews…bit-server.html
With the development of GPS controlled drones, far-reaching cheap radio equipment and tiny new computers like the Raspberry Pi, we’re going to experiment with sending out some small drones that will float some kilometers up in the air. This way our machines will have to be shut down with aeroplanes in order to shut down the system. A real act of war.
We’re just starting so we haven’t figured everything out yet. But we can’t limit ourselves to hosting things just on land anymore. These Low Orbit Server Stations (LOSS) are just the first attempt. With modern radio transmitters we can get over 100Mbps per node up to 50km away. For the proxy system we’re building, that’s more than enough.
But when time comes we will host in all parts of the galaxy, being true to our slogan of being the galaxy’s most resilient system. And all of the parts we’ll use to build that system on will be downloadable.
-
Je ne sais pas, par contre il me semble clair que si rien ne se passe Sarkozy ne peut que perdre de manière quasi mécanique. Il n'arrive pas à décoller, ou plutôt à recoller, et je pense que la dernière carte qu'il lui reste (car il a déjà tout dit et son contraire) est celle de l’évènement extérieur. A sa place je me débrouillerais pour saboter un "sommet européen de la dernière chance" (ils se tiennent à intervalles réguliers et il pourrait bien y en avoir un ou deux d'ici aux élections) et, genre, je me débrouillerais pour faire sortir la Grèce de l'Euro ou autre. Bref, un truc qui secoue la ménagère de moins 50 ans et qui par grégarisme en ces temps incertains pousse le troupeau autour de son chef.
Il s'est passé quelque chose… mais je ne pensais pas à la menace intérieure et pas à une menace de type terroriste/Breivik. Par contre je pense de plus plus que Sarkozy sera réélu. Ce n'est pas un problème de "récupération" politique ou autre mais juste un réflexe grégaire et animal.
-
Il semblerait que la dérivée (y compris la dérivée seconde) soit légèrement positive :
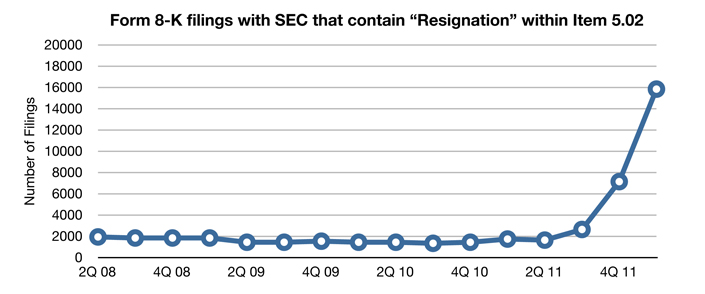
La méthodologie utilisée est la suivante (la source des chiffres est donc publique et vérifiable) : http://www.abovetopsecret.com/forum/thread818860/pg1
Then I had an idea. The Securities Exchange Act of 1934 requires that publicly traded companies must report to the SEC whenever a member of the Board or certain officers resign. Also, the SEC has a database named EDGAR that is open to the public. After a little research, I discovered that corporations must report said resignations on Form 8-K, Item 5.02. From there, it was a simple matter of searching only Form 8-Ks within a specific range of dates, and including the boolean search terms "Resigns" and "Resignation".
I felt this would at least offer us a baseline comparison to see if there is truly an uptick in resignations, or if it just appears that way. I think you will be interested in the results.
-
Faut il y voir un signe ? Il semblerait que les hautes sphères soient touchées par une grosse vague de démission des élites.
Je ne sais pas qu'elle est la fréquence "normale" de ce type de démissions. Quelqu'un sait si ça sort vraiment de l'ordinaire ?
-
Complètement d'accord mais, je vais peut-être me perdre dans des exceptions, certaines personnes âgées (je n'ai rien contre elles) au volant peuvent être tout aussi dangereuses (voire peut-être plus parfois) qu'une personne sous l'empire du cannabis ou avec 3 verres de trop. Une fois, j'ai été au supermarché du coin avec ma grand-mère (N.B. : 80 ans, conductrice occasionnelle, 500 mètres de chez elle) en voiture, j'ai cru qu'on n'y arriverait jamais vivant : refus de priorité à droite, stop grillé "je l'avais oublié" me dit-elle "tu verras quand t'auras mon âge"…
Dans ces cas là, la mise en danger de la vie d'autrui n'est pas seulement l'apanage de l'alcool, des drogues et de la vitesse. Quid de l'âge, des médicaments….C'est étrange ce 2 poids , 2 mesures.
Tu peux quand même choisir de ne pas boire. Si tu connais la formule pour éviter la dégénérescence je suis preneur.
-
Je trouve également cette campagne d'un ennui et je sens une indifférence bien plus grande qu'avec les élections précédentes. Est ce dû au fait que Sarkozy ne soit pas trop aimé et que d'un autre côté Hollande ne soit pas vraiment pris au sérieux ?
Je ne sais pas, par contre il me semble clair que si rien ne se passe Sarkozy ne peut que perdre de manière quasi mécanique. Il n'arrive pas à décoller, ou plutôt à recoller, et je pense que la dernière carte qu'il lui reste (car il a déjà tout dit et son contraire) est celle de l’évènement extérieur. A sa place je me débrouillerais pour saboter un "sommet européen de la dernière chance" (ils se tiennent à intervalles réguliers et il pourrait bien y en avoir un ou deux d'ici aux élections) et, genre, je me débrouillerais pour faire sortir la Grèce de l'Euro ou autre. Bref, un truc qui secoue la ménagère de moins 50 ans et qui par grégarisme en ces temps incertains pousse le troupeau autour de son chef.
-
Pourtant, si je ne dis pas de bêtises, d'un point de vue libéral, rouler avec 3 grs dans chaque poche, défoncé à la marie-jeanne (je fais ici abstraction de la vitesse) ne nuit pas a autrui. Du moins, il me semble. Si je roule pépère, je ne viole aucun droit naturel d'un autre citoyen.
Le problème est celui de la responsabilité : quand tu es bourré tu n'es plus vraiment responsable de tes actes (tu es responsable d'être bourré on est bien d'accord mais plus trop de ce qui suit après) et donc on peut imaginer qu'avoir des activités dangereuses soit condamnables de ce point de vue.
-
Un autre aspect de la finance centralisée est sa fragilité à la fraude : http://www.wired.co.uk/news/archive/2012-02/22/gps-spoofing
On se souviendra que le gps -spoofing fut une des techniques utilisée par les iraniens pour chopper un drone américain en douceur…
GPS "spoofers" -- devices that create false GPS signals to fool receivers into thinking that they are at a different location or different time -- could be used to defraud financial institutions, according to Todd Humphreys from the University of Texas.
On an innocuous level, GPS spoofing can lead to the confusing of in-car GPS systems so that users think they are in a different location to their actual location. However, a more sinister use could be to interfere with the time-stamping systems used in high frequency trading.
Financial institutions depend on timing that is accurate to the microsecond on a global scale so that stock exchanges in, say, London and New York are perfectly synchronised. One of the main ways of doing this is through GPS, and major financial institutions will have a GPS antenna on their main buildings. "They are always visible because they need a clear view of the sky," Humphreys told Wired.co.uk.
He explains that someone who directed a spoofer towards the antenna could cause two different problems which could have a major impact on the largely automated high-frequency trading systems. The first is simply causing confusion by manipulating the times -- a process called "time sabotage" -- on one of the global stock exchanges. This sort of confusion can be very damaging. If the automated trading systems notice something anomalous they will back out of the market; this happened in 2010 during the Flash Crash of 2.45. Secondly, it could used by an unscrupulous individual or an organisation to change the timestamp of a particular market to give them, for example, a 20 millisecond trading advantage. They could exploit that knowledge for financial gain through inter-market arbitrage.
Humphreys and his team are not simply theorising: they have created the world's most powerful GPS spoofer and have tested it on GPS-based timing devices used in mobile phone transmitters.
"So far no credible high profile attack has been recorded but we are seeing evidence of basic spoofing, likely carried out by rogue individuals or small groups," Humphreys explains. "Whilst the leap to more advanced, untraceable spoofing is large, so are the rewards. It's therefore guaranteed that criminals are looking at this. All it takes is one person to put one together and publish it online and we have a major problem."
Humphreys will be presenting his research at the GNSS Vulnerability 2012 conference on 22 February. Also to be presented at the event is the first evidence of GPS jammers being used on British roads. GPS jammers put out radio signals at the same frequency as the GPS satellites, overwhelming the devices that are used to plot positioning, including anti-theft tracking devices put into lorries with valuable loads.
The evidence of illegal jamming in the UK comes from roadside monitoring carried out by the Sentinel project -- led by Chronos Technology -- which looks at whether satellite navigation systems including GPS can be trusted by their users.
Jamming monitors have been placed at around 20 locations in the UK. One location has been monitored over six months and more than 60 individual jamming incidents were recorded in that time. Some of these might be devices used by truck drivers to prevent their boss from knowing they are using their vans out of work hours, or to fool pay-as-you-go insurance policies that use GPS data to affect pricing. Some jammers have also been confiscated by police after they've tracked down hijacked lorries.
"The problem is, the quality control on these things is really bad. Some are just 1-2 watts -- about the same as a mobile device -- but some are as powerful as 100 watts," says Bob Cockshott, Director of Position, Navigation and Timing at the ICT Knowledge Transfer Network and organiser of the GNSS Vulnerability event. "It's only a matter of time before there's an incident in the Thames estuary caused by jammers being used on land."
Cockshott calls for further regulation of jamming devices and urges businesses to make sure that they have back-up navigational systems in place.
-
Dette grecque : réunion en coulisse d'un groupe de banquiers et d'investisseurs
Un groupe de représentants de 15 grandes banques, fonds d'investisements et fonds spéculatifs se réunit jeudi 1er mars pour décider si la restructuration de la dette de la Grèce doit déclencher des paiements pour les détenteurs de titres dérivés, écrit mercredi le Wall Street Journal. Ces paiements peuvent représenter plusieurs milliards de dollars, alors qu'Athènes est proche d'un défaut de paiement.
Le groupe doit se retrouver jeudi matin pour décider si la restructuration de dette de la Grèce est à même de déclencher des paiements pour les détenteurs de titres de couverture de défaillance ou "credit default swap" (CDS), qui fonctionnent comme une assurance contre un événement, explique le Wall Street Journal. L'impact de cette décision pourrait dépasser le marché de la dette grecque et est à même d'affecter les investisseurs à travers les marchés d'obligations européens ainsi que les détenteurs de 2 900 milliards de CDS sur la dette de gouvernements dans le monde.
PAS D'APPEL POSSIBLE
Mais certains investisseurs se plaignent du secret entourant le processus et l'accusent d'être plein de conflits d'intérêt, poursuit le quotidien financier. Aucune personne extérieure ne peut participer à la réunion qui est organisée par l'association des swaps et dérivés internationaux, et aucun compte rendu ne sera distribué. Quand une décision sera annoncée, avant lundi, le comité ne fournira pas d'explication. Il n'y aura pas de possibilité de faire appel pour les investisseurs.
Si les sociétés qui participent au comité sont connues, comme Goldman Sachs Group, Deutsche Bank et Morgan Stanley, les noms de leurs représentants ne sont pas rendus publics, de même que l'exposition de chaque firme ou personne à la dette grecque. L'argent en jeu dans les CDS grecs n'est pas énorme, et il ne devrait pas y avoir plus de 3,2 milliards de dollars de paiements nets entre les acheteurs et vendeurs de protections contre le défaut ou la restructuration de dette.
-
Les drones sont une formidable avancée technologique, moins coûteux et surtout, la vie des pilotes est épargné. Ne soyons pas contre cette technologie, ce ne sont pas les technologies qui sont dangereuses ce sont ceux qui les utilisent.
Oui mais c'est un peu rapide. Dans le dossier de cato indiqué par G7H+ il y a un article sur le fait qu'en faisant baisser les coûts ça crée une incitation plus forte à les utiliser et donc in fine à abaisser le niveau à partir du quel on commence un conflit armé.
Il me parait clair que ce sont des raisons de ce type qui ont permis de nombreuses interventions récemment (notamment la Lybie). Dire que c'est forcément une bonne chose est un peu rapide surtout si l'on constate que les drones sont plutôt des technologies favorisants l'agresseur que l'agressé.
-
A lire sur le sujet, l'opinion de Rogoff économiste et Grand-Maître d'échecs : http://www.chessbase…asp?newsid=7372
Technology and Inequality
By Kenneth Rogoff
CAMBRIDGE – Until now, the relentless march of technology and
globalization has played out hugely in favor of high-skilled
labor, helping to fuel record-high levels of income and wealth
inequality around the world. Will the endgame be renewed class
warfare, with populist governments coming to power, stretching
the limits of income redistribution, and asserting greater state
control over economic life?
There is no doubt that income inequality is the single biggest
threat to social stability around the world, whether it is in the
United States, the European periphery, or China. Yet it is easy
to forget that market forces, if allowed to play out, might
eventually exert a stabilizing role. Simply put, the greater the
premium for highly skilled workers, the greater the incentive to
find ways to economize on employing their talents.
The world of chess, with which I am closely familiar, starkly
illustrates the way in which innovation in the coming decades may
have a very different effect on relative wages than it did over
the past three decades.
During the late eighteenth and early nineteenth centuries, a
brilliantly inventive chess-playing “automaton” toured the
world’s capitals. “The Turk” won games against the likes of
Napoleon and Benjamin Franklin, while challenging many great
minds to penetrate its secrets. Concealing a human player in a
shifting compartment amid a maze of impressive-looking gadgetry,
it took decades for outsiders to correctly guess how the Turk
really worked.
Today, the scam has been turned on its head: chess-playing
machines pretend to be chess-playing humans. Desktop-based chess
programs have considerably surpassed the best human players over
the past decade, and cheating has become a growing scourge. The
French chess federation recently suspended three of its top
players for conspiring to obtain computer
assistance. (Interestingly, one of the main ways to uncover
cheating is by using a computer program to detect whether a
player’s moves consistently resemble the favored choices of
various top computer programs.)
Of course, there are many other examples of activities that were
once thought exclusively the domain of intuitive humans, but that
computers have come to dominate. Many teachers and schools now
use computer programs to scan essays for plagiarism, an ancient
transgression made all too easy by the Internet. Indeed,
computer-grading of essays is a surging science, with some
studies showing that computer evaluations are fairer, more
consistent, and more informative than those of an average
teacher, if not necessarily of an outstanding one.
Expert computer systems are also gaining traction in medicine,
law, finance, and even entertainment. Given these developments,
there is every reason to believe that technological innovation
will lead ultimately to commoditization of many skills that now
seem very precious and unique.
My Harvard colleague Kenneth Froot and I once studied the
relative price movements of a number of goods over a 700-year
period. To our surprise, we found that the relative prices of
grains, metals, and many other basic goods tended to revert to a
central mean tendency over sufficiently long periods. We
conjectured that even though random discoveries, weather events,
and technologies might dramatically shift relative values for
certain periods, the resulting price differentials would create
incentives for innovators to concentrate more attention on goods
whose prices had risen dramatically.
Of course, people are not goods, but the same principles
apply. As skilled labor becomes increasingly expensive relative
to unskilled labor, firms and businesses have a greater incentive
to find ways to “cheat” by using substitutes for high-price
inputs. The shift might take many decades, but it also might come
much faster as artificial intelligence fuels the next wave of
innovation.
Perhaps skilled workers will try to band together to get
governments to pass laws and regulations making it more difficult
for firms to make their jobs obsolete. But if the global trading
system remains open to competition, skilled workers’ ability to
forestall labor-saving technology indefinitely should prove
little more successful than such attempts by unskilled workers in
the past.
The next generation of technological advances could also promote
greater income equality by leveling the playing field in
education. Currently, educational resources – particularly
tertiary educational resources (university) – in many poorer
countries are severely limited relative to wealthy countries,
and, so far, the Internet and computers have exacerbated the
differences.
But it does not have to be that way. Surely, higher education
will eventually be hit by the same kind of sweeping wave of
technology that has flattened the automobile and media
industries, among others. If the commoditization of education
eventually extends to at least lower-level college courses, the
impact on income inequality could be profound.
Many commentators seem to believe that the growing gap between
rich and poor is an inevitable byproduct of increasing
globalization and technology. In their view, governments will
need to intervene radically in markets to restore social balance.
I disagree. Yes, we need genuinely progressive tax systems,
respect for workers’ rights, and generous aid policies on the
part of rich countries. But the past is not necessarily prologue:
given the remarkable flexibility of market forces, it would be
foolish, if not dangerous, to infer rising inequality in relative
incomes in the coming decades by extrapolating from recent
trends.
-
Les USA ressemblent de plus en plus à un état policier…
source : http://www.cbsnews.c…-their-laptops/
Judge: Americans can be forced to decrypt their laptops
(CNET) - American citizens can be ordered to decrypt their PGP-scrambled hard
drives for police to peruse for incriminating files, a federal judge in Colorado ruled
today in what could become a precedent-setting case.
Judge Robert Blackburn ordered a Peyton, Colo., woman to decrypt the hard drive
of a Toshiba laptop computer no later than February 21--or face the consequences
including contempt of court.
Blackburn, a George W. Bush appointee, ruled that the Fifth Amendment posed no
barrier to his decryption order. The Fifth Amendment says that nobody may be
"compelled in any criminal case to be a witness against himself," which has become
known as the right to avoid self-incrimination.
"I find and conclude that the Fifth Amendment is not implicated by requiring production
of the unencrypted contents of the Toshiba Satellite M305 laptop computer," Blackburn
wrote in a 10-page opinion today. He said the All Writs Act, which dates back to 1789
and has been used to require telephone companies to aid in surveillance, could be
invoked in forcing decryption of hard drives as well.
Ramona Fricosu, who is accused of being involved in a mortgage scam, has declined to
decrypt a laptop encrypted with Symantec's PGP Desktop that the FBI found in her
bedroom during a raid of a home she shared with her mother and children (and whether
she's even able to do so is not yet clear).
"I hope to get a stay of execution of this order so we can file an appeal to the 10th Circuit
Court of Appeals," Fricosu's attorney, Phil Dubois, said this afternoon. "I think it's a matter
of national importance. It should not be treated as though it's just another day in Fourth
Amendment litigation."
Dubois said that, in addition, his client may not be able to decrypt the laptop for any number
of reasons. "If that's the case, then we'll report that fact to the court, and the law is fairly
clear that people cannot be punished for failure to do things they are unable to do," he said.
Today's ruling from Blackburn sided with the U.S. Department of Justice, which argued, as
CNET reported last summer, that Americans' Fifth Amendment right to remain silent doesn't
apply to their encryption passphrases. Federal prosecutors, who did not immediately respond
to a request for comment this afternoon, claimed in a brief that:
Public interests will be harmed absent requiring defendants to make available unencrypted
contents in circumstances like these. Failing to compel Ms. Fricosu amounts to a concession to
her and potential criminals (be it in child exploitation, national security, terrorism, financial crimes
or drug trafficking cases) that encrypting all inculpatory digital evidence will serve to defeat the
efforts of law enforcement officers to obtain such evidence through judicially authorized search
warrants, and thus make their prosecution impossible.
While the U.S. Supreme Court has not confronted the topic, a handful of lower courts have.
In March 2010, a federal judge in Michigan ruled that Thomas Kirschner, facing charges of receiving
child pornography, would not have to give up his password. That's "protecting his invocation of
his Fifth Amendment privilege against compelled self-incrimination," the court ruled.
A year earlier, a Vermont federal judge concluded that Sebastien Boucher, who a border guard
claims had child porn on his Alienware laptop, did not have a Fifth Amendment right to keep the files
encrypted. Boucher eventually complied and was convicted.
Prosecutors in this case have stressed that they don't actually require the passphrase itself, and
today's order appears to permit Fricosu to type it in and unlock the files without anyone looking over
her shoulder. They say they want only the decrypted data and are not demanding "the password to
the drive, either orally or in written form."
Because this involves a Fifth Amendment claim, Colorado prosecutors took the unusual step of
seeking approval from headquarters in Washington, D.C.: On May 5, Assistant Attorney General
Lanny Breuer sent a letter to Colorado U.S. Attorney John Walsh saying "I hereby approve your
request."
The question of whether a criminal defendant can be legally compelled to cough up his encryption
passphrase remains an unsettled one, with law review articles for at least the last 15 years arguing
the merits of either approach. (A U.S. Justice Department attorney wrote an article in 1996, for
instance, titled "Compelled Production of Plaintext and Keys.")
Much of the discussion has been about what analogy comes closest. Prosecutors tend to view
PGP passphrases as akin to someone possessing a key to a safe filled with incriminating documents.
That person can, in general, be legally compelled to hand over the key. Other examples include
the U.S. Supreme Court saying that defendants can be forced to provide fingerprints, blood
samples, or voice recordings.
On the other hand are civil libertarians citing other Supreme Court cases that conclude Americans
can't be forced to give "compelled testimonial communications" and extending the legal shield of the
Fifth Amendment to encryption passphrases. Courts already have ruled that that such protection
extends to the contents of a defendant's minds, the argument goes, so why shouldn't a passphrase
be shielded as well?
Fricosu was born in 1974 and living in Peyton as of 2010. She was charged with bank fraud, wire
fraud, and money laundering as part of an alleged attempt to use falsified court documents to illegally
gain title to homes near Colorado Springs that were facing "imminent foreclosure" or whose owners
were relocating outside the state. Some of the charges could yield up to 30 years in prison; she pleaded
not guilty. Her husband, Scott Whatcott, was also charged.
Un seul conseil : plausible deniability et un logiciel : truecrypt.
-
sarkommence, j'aurais écrit…
sarcomence plutôt à cause de l'aspect maladif et cancéreux du pouvoir.



Armageddon économique ?
dans Economie
Posté
Hanan dans ses oeuvres :
1GrxHDyXyj8